There is currently debate amongst the politicians in the US, UK and elsewhere about providing a security backdoor, so “officially approved” groups such as the NSA or FBI can monitor the activities “if needed” – to protect us all from terrorists, of course.
Well, what’s interesting is we have a real life example unfolding where the NSA created a weakness in an encryption protocol (Dual_EC, a pseudo-random number generator) some years ago, and this has enabled an exploitation to gain access to traffic through Juniper Networks’ firewalls.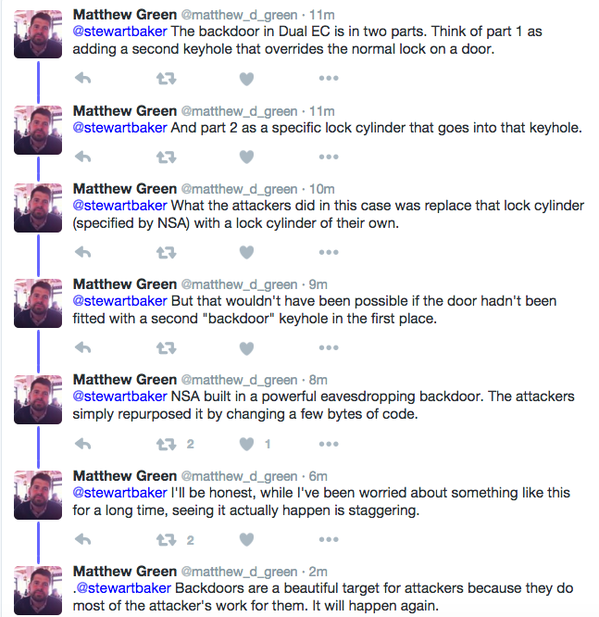
This is EXACTLY the concern that the security community has been concerned about in this uninformed “debate”. Once you create a backdoor, somebody else can repurpose that backdoor.
This article discusses the issue in more detail, and this blog post by Matthew Green explains it all beautifully.
In my opinion, however, the imposition of such backdoors is inevitable. There will be no place for anyone or any business to protect themselves or their information from the state, and hence from anyone committed to accessing it. As I’ve said, we’ll have sufficient false flag events to “justify” its elimination, and it’ll be completed globally, in my opinion, within two years at the outside.
Watch this space…

Recent Comments